The official Sucuri WordPress plugin comes with tools that checks the integrity of the core WordPress files which are the PHP, JavaScript, CSS, and other files that come with the official release. The core integrity checks are powered by two main parts: an HTTP request that communicates with an official WordPress API service and an implementation of a checksum reader.
A checksum or hash sum is a small-size datum from a block of digital data for the purpose of detecting errors which may have been introduced during its transmission or storage. It is usually applied to an installation file after it is received from the download server – Definition from WikiPedia.
The plugin uses this checksum to detect if a file has been added, modified or deleted. You must know that the plugin only checks the content of the WordPress core files and will not be able to check .
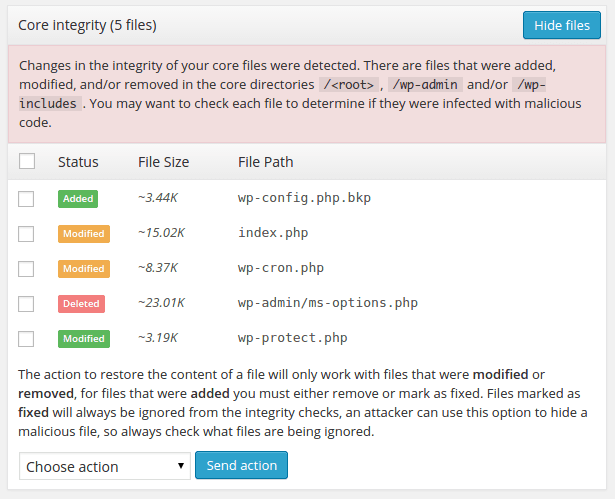
Explanation of the Warning
Consider the scenario where you have two files named abc.txt and xyz.txt with the content “Lorem ipsum dolor” and “Hello world” respectively. Below you will see the execution of the command md5sum which provides a virtually unique identifier for the data inside each file. This example is very simple but in most cases, you would not have the time and patience to manually check the contents of each file, so you would just scan the directory and retrieve the checksum of all the files inside it. Then compare them with the checksum of the original file.
$ echo 'Lorem ipsum dolor' > abc.txt
$ echo 'Hello world' > xyz.txt
$ md5sum abc.txt xyz.txt
e2080afd6dbec7ab31aa3ce1e2c60073 abc.txt
f0ef7081e1539ac00ef5b761b4fb01b3 xyz.txtEvery time you create a file with the same data, it will have the same unique identifier. The name of the files is not relevant for the evaluation so you could have twenty files with the text “Hello world” all with different names and all of them will result with the same checksum.
$ for i in {1..7}; do
filename="testcase-$RANDOM.txt";
echo 'Hello world' > $filename;
md5sum $filename;
done
f0ef7081e1539ac00ef5b761b4fb01b3 testcase-8832.txt
f0ef7081e1539ac00ef5b761b4fb01b3 testcase-11529.txt
f0ef7081e1539ac00ef5b761b4fb01b3 testcase-16161.txt
f0ef7081e1539ac00ef5b761b4fb01b3 testcase-17813.txt
f0ef7081e1539ac00ef5b761b4fb01b3 testcase-30147.txt
f0ef7081e1539ac00ef5b761b4fb01b3 testcase-23397.txt
f0ef7081e1539ac00ef5b761b4fb01b3 testcase-23348.txtBy comparing the checksum of a file, you can learn if someone have modified its content. This is pretty common when a malicious person attacks your website and gets access to an administrative resource like the credentials of a user. They will try to keep the access even if these credentials are changed so they hide malicious code generally known as a “backdoor” inside a core file.
What do you do with added files?
When a file is marked as added, it means that it was not found in the official WordPress archives for the version number detected in your current website. For example, if your site has a file named wp-protect.php in the document root and the official WordPress archives do not come with this file. This doesn’t always mean that it is malicious, but it does mean that it wasn’t originally there.
However, some people like to upload a number of files in their website to facilitate its download or for any other reason you can think of. In this case, the file may not be malicious, but the plugin does not know that. It only cares about the integrity of the core files not the content of the files.
At the bottom of the “Core Integrity” panel, you will find a dropdown with a button that you can use to execute an action over the selected files. For files that were added, you can choose to delete them or mark them as fixed. If you do not trust the file(s), then you should consider deleting them as they probably do not belong. If you trust the file(s), then you can force the plugin to ignore them in future scans by marking them as fixed.
What to do with Deleted Files
When a file is marked as deleted, it means that it was found in the official WordPress archives, but not in your website files. You will not see this frequently because, when a file is deleted from the core directories, the site generally goes down, but there may be some exceptions like the xmlrpc.php file which is used by WordPress to allow users and services to interact with the site through RPC.
In this case, there is only one solution which is to restore the files fetching its original content from the official WordPress repositories. The plugin provides an option to do this automatically so you do not have to go through the process of manually finding and restoring these files.
What do I do with Modified Files?
When a file is marked as modified, it means that it was found in the official WordPress archives and the website, but its content is different which is detected comparing their checksums. You should never modify core files of any CMS because this complicates upgrades and maintainability of the code. If you find modified files, you must select them all and choose the option to restore their original content.
