The Sucuri Firewall provides two modes for SSL connections: Partial HTTPS and Full HTTPS. They are available on the “HTTPS/SSL” tab of the Firewall dashboard.
Partial HTTPS
The connection is safe (HTTPS) between your visitor and the Firewall, however when reaching your server, the connection uses cleartext HTTP (not secure).
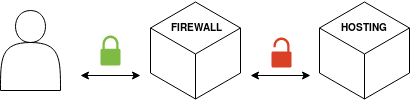
Although your visitor will see the website as safe, Partial HTTPS is known for causing redirect loops and could suffer from man-in-the-middle (MitM) attacks. Use it only if completely necessary.
Full HTTPS
The safest way of configuring the SSL Mode, Full HTTPS is designed to make the whole connection encrypted:
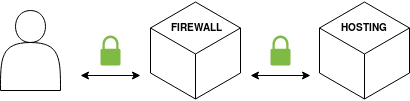
This method requires an SSL certificate on the server side. Beware that your visitor will never see the hosting SSL certificate, only the Firewall itself does. Your visitors will always see the SSL certificate uploaded on the Firewall.
The hosting SSL certificate could be a self-signed SSL certificate or even an expired SSL certificate (you do not need to renew your server SSL certificate). The Firewall will continue to accept the server SSL certificate and always provide your visitors the SSL certificate within the Firewall. However, in case you want a Strict SSL mode so the Firewall always check if the server SSL certificate is valid, please open a support ticket.
NOTE: For HTTPS requests, when using Partial HTTPS, the WAF will reach your server at port 80; when using Full HTTPS, the WAF will reach at port 443. This is hard coded and cannot be customized.
