The kill chain model was created by Lockheed Martin’s CIRT (incident response group)" to identify and categorize each stage of a network-based (cyber) attack. They followed the same concept used by the US military to structure their own attacks, which consisted of target identification, force dispatch to target, decision and order to attack the target, and finally the destruction of the target.
When applied to information security (and computer attacks), they divided the kill chain into 7 stages (phases):
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control (C2)
- Actions on Objectives
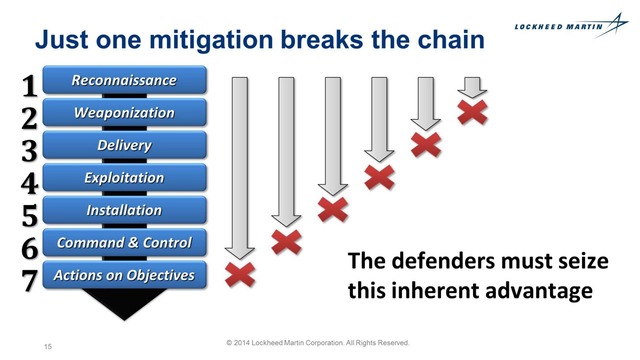
Each stage is required in order to achieve the next one, so focusing your defenses on the earlier stages (and during all phases) will prevent a successful compromise. When you start to think about these stages of your security posture, you can easily identify what you need to improve. We recommend reading the full PDF here to understand the whole model: http://www.lockheedmartin.ca/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf
Sucuri Firewall and the Intrusion Kill Chain
The Sucuri Firewall (WAF) runs on top of our high performance anycast network (CDN) and provides an IPS (Intrusion Prevention System) and WAF (Web Application Firewall) directly from the Cloud without the need to install anything on your end. When you think about the Kill Chain, the Website Firewall covers every single stage, giving you complete protection against today’s website attacks.
- Reconnaissance: Our Firewall blocks web directory guessing, vulnerability scanners, discovery bots and also hides the real IP address of your website. We also send every log through our LIDS (Log-based Intrusion Detection) engine, which blocks attackers during their reconnaissance phase.
- Weaponization: Most attackers use similar techniques and tools (eg: MetaSploit) to Weaponize their attack and we block payloads used by most weaponization engines.
- Delivery: Our Firewall runs as WAF + IPS inline, blocking the delivery of malicious payloads to your site.
- Exploitation: In addition to the malicious payload inspection, we also virtually patch and have an inteligent engine to protect against vulnerability exploitations that are used during this phase (SQL Injections, XSS, RCE, etc).
- Installation: Our firewall also inspects file uploads, looking for backdoors, trojans and similar malware content. That allows us to block the post-exploitation and installation of malicious code.
- Command and Control (C2): We spend many hours investigating backdoor traffic and how they are used to communicate with compromised sites and we use the result of this research to better detect and auto-block them through our Firewall.
- Actions on Objectives: We provide multiple access-control options by default that also help to block an attacker from achieving their objectives in case all other steps fail. It includes our virtual hardening, admin page restrictions and many other features.
If you have any questions on the capabilities of our Sucuri Firewall and how it can help make your site more secure, let us know.
